-
Notifications
You must be signed in to change notification settings - Fork 149
Identity Components LDAP and Single Sign On
The geoportal implements a standard Java container-based authentication pattern. The Java container is configured to authenticate against an identity store. Inbound requests are processed by the container and credentials are requested for and authenticated as required. Information about the authenticated user is then supplied, per request, to each participating web application running within the container. This information is supplied as a UserPrincipal object, which typically holds a "username" credential, the "password" credential is not provided to the underlying applications. The primary components associated with authentication, authorization, identification and self-care are identified in the figure below.
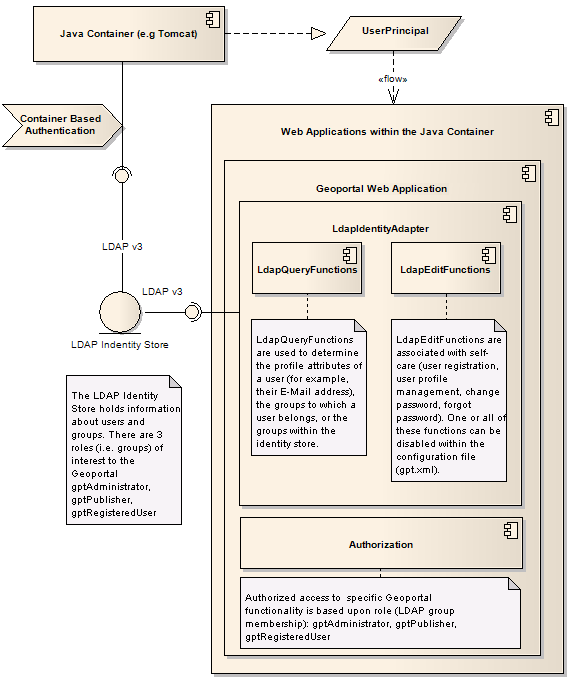
At a minimum, the geoportal requires read access to an external LDAP (Lightweight Directory Access Protocol) identity store. The identity store holds information about users and groups. A set of functions query the identity store (read only) to determine the attributes associated with a user (e.g. E-Mail address), the groups to which a user belongs, and the groups within the store. Authorized access to specific functionality is based upon group membership (i.e. role), defined below:
- Geoportal Administrator: group members have full access, including the ability to approve metadata documents
- Geoportal Publisher: group members can publish metadata documents and register remote sites for harvesting
- Geoportal RegisteredUser: group members can save searches and maps for later use