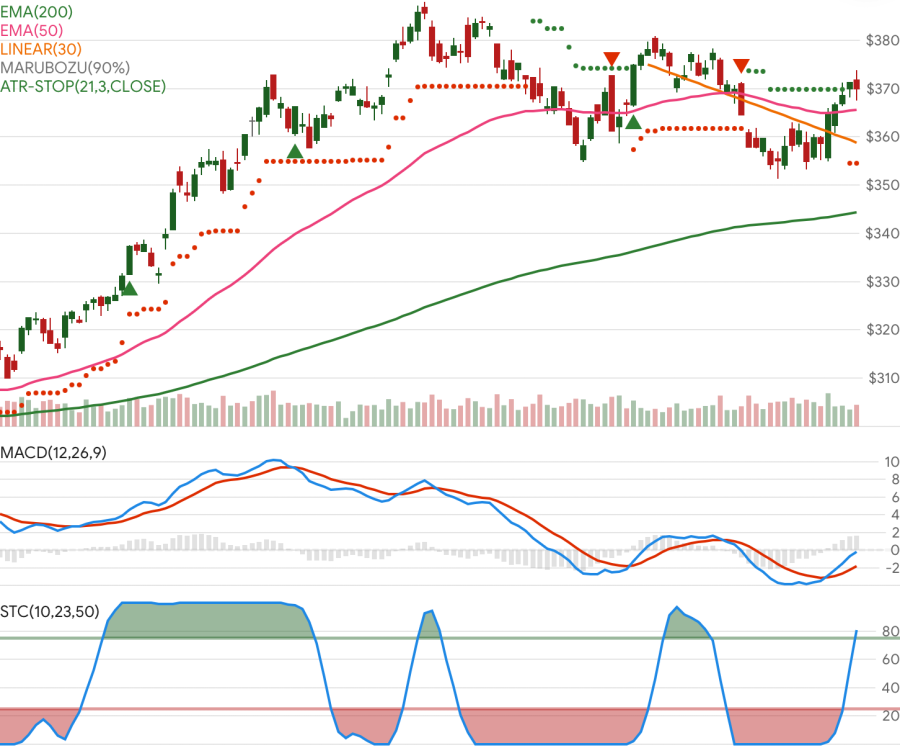
This is a demo of the Skender.Stock.Indicators NuGet package. It is an Angular website with a Chart.js financial/candlestick stock chart, with a .NET Web API backend to generate indicators. The indicator library can be implemented in any .NET compatible ecosystem (it does not have to be in an API like this). See the library documentation for more examples, the user guide, and a full list of available indicators.
Live demo site: charts.StockIndicators.dev
This repo and charting tool is primarily intended to demonstrate the Stock Indicators for .NET library. It is not meant to be a fully featured charting system and may not be an architectural model that works for your use case. If you need a mature charting tool, please explore all of your charting and visualization options.
If you want to host on your local computer and review the source code, follow the instructions below.
- Git and Node.js
- Visual Studio
-
Open
\server\ChartBackend.slnin Visual Studio. Take note of the URL in the WebApi project properties. -
Select
WebApiproject and run by eitherCTRL+F5ordotnet runCLI command. You can also View from right-click menus. If you've done this successfully, a browser window will open and say "API is functioning nominally." Leave the browser window open. -
Open
client\src\environments\environment.tsand modify the API URL, if needed, then save file.export const env: EnvConfig = { production: false, api: 'https://localhost:44392' };
-
Open
Git Bashwindow and navigate to the\clientfoldernpm install npm start
The web application should launch automatically.
Optionally, if you intend to use the local Azure storage emulator to get and store local quote data from the Alpaca API, you'll also need to set some local environment variables and run the ‘Functions.csproj‘ project. Use your own key and secret values.
setx ALPACA_KEY "YOUR ALPACA API KEY"
setx ALPACA_SECRET "YOUR ALPACA SECRET KEY"
setx AzureWebJobsStorage "UseDevelopmentStorage=true"This repository includes a Dev Container configuration to provide a consistent development environment. The Dev Container includes the following tools and dependencies:
- .NET SDK 9
- Node LTS
- NPM latest
- GitHub CLI
- Angular CLI
- Azure Functions Core Tools
- PowerShell
- ESLint
-
Install Visual Studio Code and the Remote - Containers extension.
-
Clone the repository and open it in Visual Studio Code.
-
When prompted, reopen the repository in the Dev Container.
-
The Dev Container will be built and started automatically. You can now use the integrated terminal and other tools within the Dev Container.
The Dev Container includes the following environment variables:
ALPACA_KEYALPACA_SECRETAzureWebJobsStorage
These environment variables are required for fetching quote data from the Alpaca API and for local development and debugging of Azure Functions.
To securely store and manage secrets such as ALPACA_KEY and ALPACA_SECRET, you can use Azure Key Vault. Follow the steps below to set up and use Azure Key Vault for storing secrets.
-
Create an Azure Key Vault in your Azure subscription.
-
Add the
ALPACA_KEYandALPACA_SECRETsecrets to the Key Vault. -
Update the application code to retrieve these secrets from Azure Key Vault during runtime.
-
Ensure that the necessary permissions are granted to the application to access the Key Vault.
-
Update the
local.settings.jsonfile in theserver/Functionsdirectory to include theALPACA_KEYandALPACA_SECRETenvironment variables. -
Update the
README.mdto include instructions for setting up and using Azure Key Vault for storing secrets.
For local development, you can use User Secrets to store sensitive information such as ALPACA_KEY and ALPACA_SECRET. Follow the steps below to set up and use User Secrets for local development.
-
In the
server/Functionsdirectory, run the following command to initialize User Secrets:dotnet user-secrets init
-
Add the
ALPACA_KEYandALPACA_SECRETsecrets to User Secrets:dotnet user-secrets set "ALPACA_KEY" "YOUR_ALPACA_API_KEY" dotnet user-secrets set "ALPACA_SECRET" "YOUR_ALPACA_SECRET_KEY"
-
Update the application code to retrieve these secrets from User Secrets during runtime.
-
Ensure that the necessary permissions are granted to the application to access the User Secrets.
-
Update the
README.mdto include instructions for setting up and using User Secrets for local development.
This is an open-source project. If you want to report bugs, contribute fixes, or add new indicators, please review our contributing guidelines.