-
-
Notifications
You must be signed in to change notification settings - Fork 700
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Private/secret databases: database files that are only visible to plugins #950
Comments
|
The alternative to this would be to use regular databases and control access to them using Authentication and permissions. My concern there is that it's just too easy for someone to mess up their configuration, which would be really bad. I like the idea of a much stronger defense mechanism specifically designed for secrets that should not be exposed. Outside of secrets, passwords and tokens this mechanism could also be useful for the use-case of using Datasette to power websites - as seen on https://www.niche-museums.com/ and https://www.rockybeaches.com/ - maybe those sites don't want to expose their data through their API but still want to use |
|
|
|
Naming challenge: secret databases or private databases? I prefer private. But |
|
Forcing people to spell out |
|
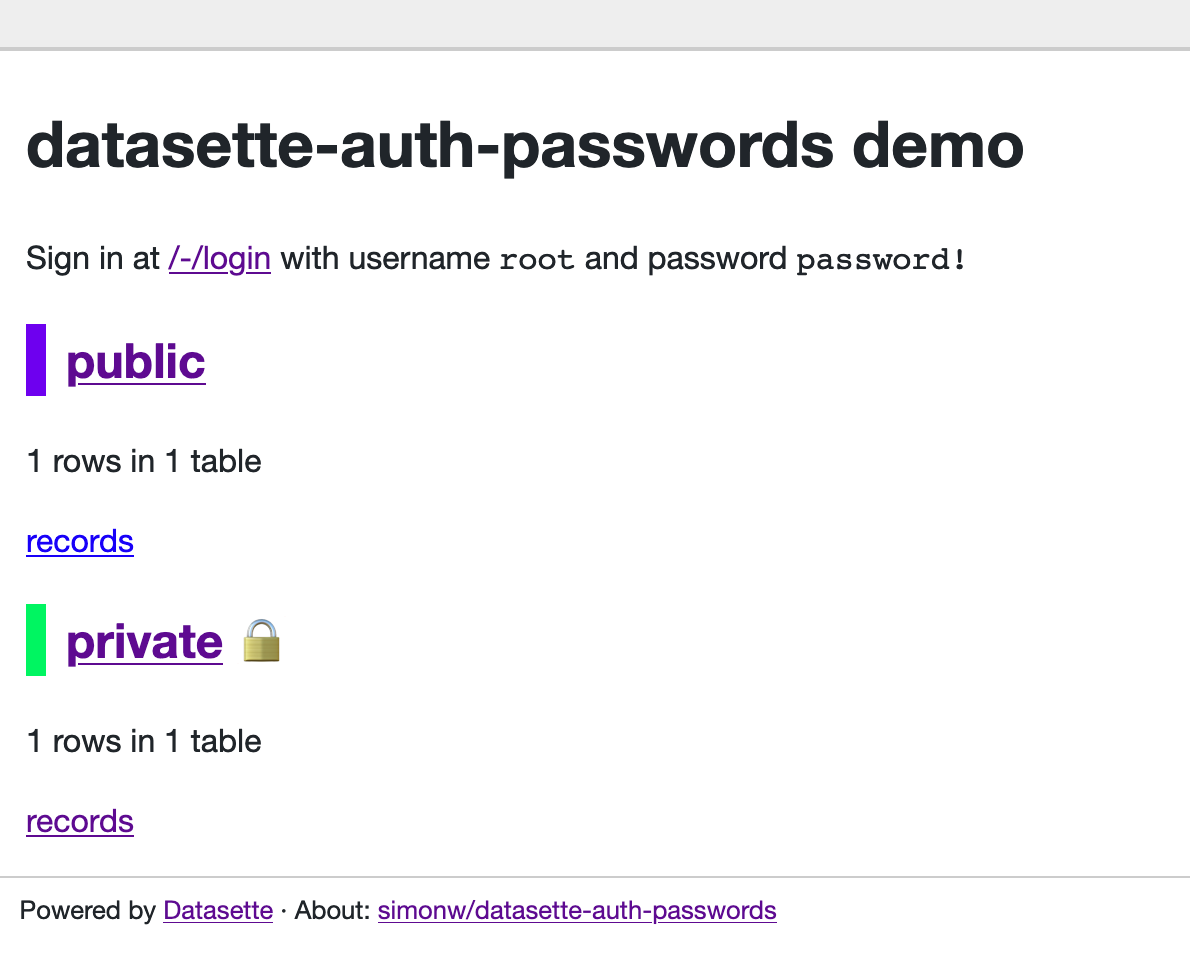
The problem with the term "private" is that it could be confused with the concept of databases that aren't visible to the public due to the permissions system - the ones that are displayed with the padlock icon e.g. on https://datasette-auth-passwords-demo.datasette.io/ So I think "secret" is a better term for these. |
|
Closing this issue in favour of this one: |
In thinking about the best way to implement simonw/datasette-auth-passwords#6 (SQL-backed user accounts for
datasette-auth-passwords) I realized that there are a few different use-cases where a plugin might want to store data that isn't visible to regular Datasette users:Idea: allow one or more private database files to be attached to Datasette, something like this:
The
secrets.dbfile would not be visible using any of the Datasette's usual interface or API routes - but plugins would be able to run queries against it.So
datasette-auth-passwordsmight then be configured like this:The plugin could even refuse to operate against a database that hadn't been loaded as a secret database.
The text was updated successfully, but these errors were encountered: