There are two main steps required to set up SSO using Okta on ImageKit:
{% hint style="info" %} Okta subscription
Although you may use a free developer account on Okta to set up and test the SSO application, having a premium Okta subscription is recommended for seamless role provisioning for your users. Read more here. {% endhint %}
First, you need to create an application on Okta and generate an IdP Metadata XML file.
You may refer to the official documentation by Okta here or follow our brief guide below:
- Log in to the Okta portal and open the organization admin panel
- Navigate to the "Applications" screen using the side navigation menu
- Click the "Create App Integration" button
- In the modal popup that opens, choose the "SAML 2.0" radio button as shown below, then click "Next"
- Input a name for the application, we will use "ImageKit" for this guide, then click "Next"
On the next screen, we will configure various authentication parameters as shown:
| Field | Value |
|---|---|
| Single sign-on URL | https://imagekit.io/saml/consume |
| Audience URI | https://imagekit.io/saml/consume |
| Default RelayState | https://imagekit.io/dashboard |
| Name ID format | EmailAddress |
| Application username | Email |
| Update application username on | Create and update |
Note: Name ID is the unique email address of the user that will be used to identify them on ImageKit.
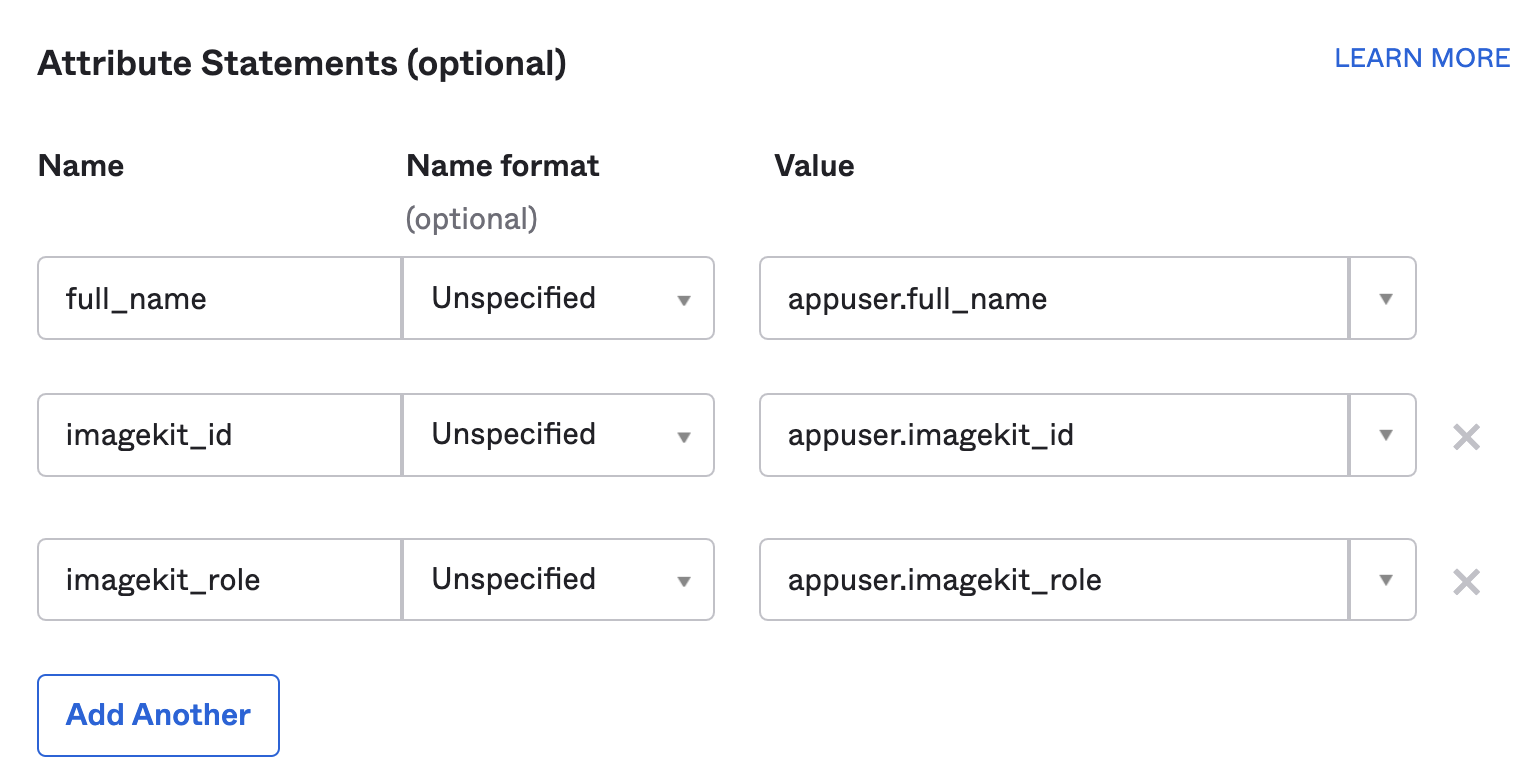
Now you need to specify three more keys that ImageKit uses to authorize and provision your users:
| Field | Description | Claim composition |
|---|---|---|
| imagekit_id | The ImageKit ID of your organization account. | <your_imagekit_id> |
| full_name | The full name of the user. It can be a combination of their first name and last name in the Okta universal directory. | e.g. appuser.full_name which should internally map to user.firstName + " " + user.lastName |
| imagekit_role | The role to assign to the user on ImageKit that would decide their access privileges. Accepted values of this key in the SAML response sent to ImageKit are:
Read more about different ImageKit roles and their privileges here. |
The final computed value of this claim must be one of the accepted role strings from the list specified alongside. |
To do this, you need to create "Profile Mappings" on Okta. Read the official guide here or follow the quick version below.
Navigate to "Directory > Profile Editor", and create user attributes that will be mapped and sent to ImageKit during authentication.
Back on the SSO application page under the SAML section, ensure that these fields are included correctly in your Okta user object.
Assign the application to users as shown below to finish this step.
Navigate to the SAML setup instructions screen and scroll to the section with the IdP Metadata XML file. Copy and save it in a safe location. You will need to upload this XML file to your ImageKit account in a later step.
Refer to the official Okta guide to assign the ImageKit application to Okta users.
If you have administrator privileges on your ImageKit account, you can enable SSO for all the users in your account as follows:
- Navigate to the Settings page.
- Open the IdP Metadata XML file (which was downloaded previously) in a text editor of your choice.
- Copy and paste the entire contents of the file into the Metadata XML input box.
- Click on the 'Save' button.
Your users should now be able to use Okta SSO to log into ImageKit.
SSO users would need to initiate their very first login on ImageKit through the ImageKit app by navigating to their end-user dashboard on Okta.
After their first login, they may use the ImageKit SSO login page for signing in to ImageKit directly. Read more here.
You can disable SSO login for the users on your ImageKit account by deleting the Metadata XML.
To do so, navigate to the Settings page and click on the 'Delete' button.
If you face any issues while using these features or have a question or suggestion, please reach out to us at [email protected].