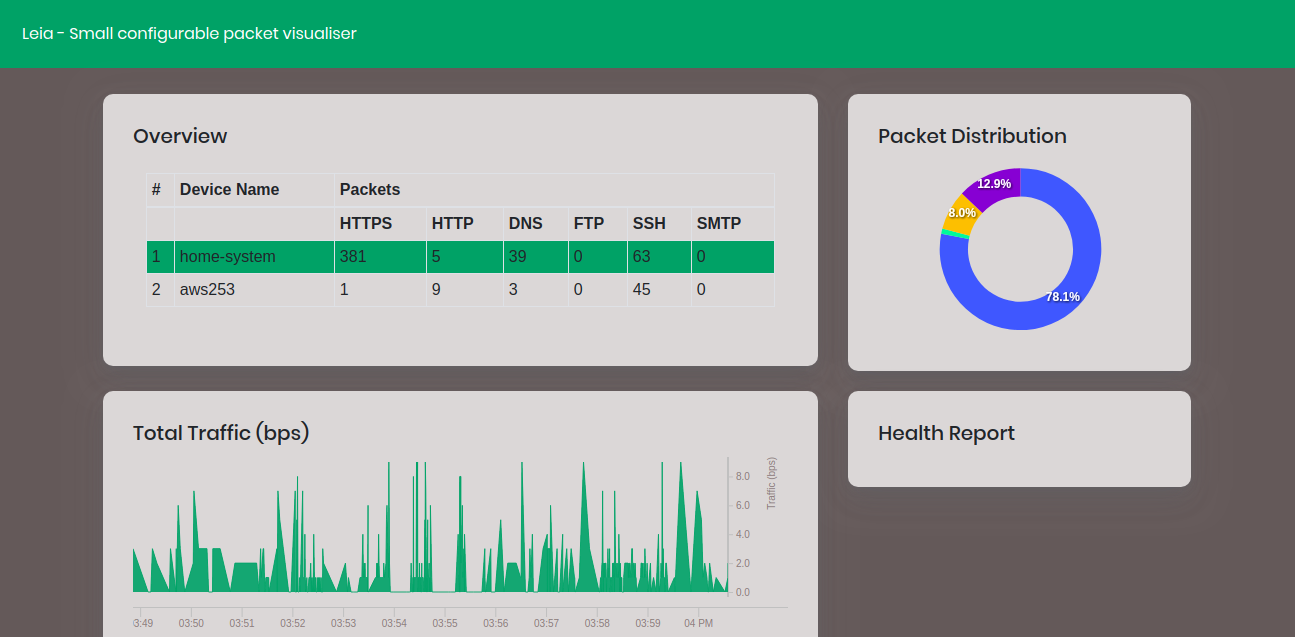
Leia is a tiny-configurable network monitoring service accross multiple Linux distros.
The aim of the project is to easily monitor packets for different protocols(HTTP,SMTP etc.) across different Linux based servers with minimum packet-loss.
Leia uses tcpdump to capture the packets,which in turn require sudo priviledges.The 2 possible solutions I could think of,were-
- Run the server with sudo priviledges (not at all recommended,why)
sudo node server.js - Create a group named
pcapwhich has the permission to executetcpdumpand add the user executing theclient/server.js(check permission.sh)
Leia clients publish the packets on a nats-queue, the nats uses its own tcp protocol under the hood.On the other hand, the leia-admin app works inside browser and can thus only talk through http or websocket like protocol.
Thus, we need a relay to forward all the websocket or http request(websocket in our case) to the tcp based nats-queue.
- Start the nats-server using
nats-server - Configure your server and start the server in the background using PM2.
pm2 start server.js - Command your server to start publishing the specific packets using curl
//To start capturing HTTPS packets
curl http://localhost:8080/api/start/https
//To stop capturing HTTPS packets
curl http://localhost:8080/api/stop/https
//To start capturing DNS packets
curl http://localhost:8080/api/start/dns
//To stop capturing DNS packets
curl http://localhost:8080/api/stop/dns
- Currently the following protocols are supported-HTTP,HTTPS,FTP,DNS,SSH and SMTP
- Start the relay server using
ws-tcp-relay <tcpTargetAddress> - Configure your leia-admin app
- Goto
client/utils/net-utils.js - Add the port for your protocol inside the PROT_TO_PORT object
const PROT_TO_PORT = {
http: 80,
https: 443,
....
YOUR_PROTOCOL:PORT_NUMBER
}- Mark the process ID as -1 for the same protocol
const PROT_TO_PID = {
http: -1,
https: -1,
....
YOUR_PROTOCOL:-1
}-
Capture packets in real time and pipeline to a messaging queue.
-
Visualise the traffic using a react-redux administration app.
-
Encrypt the data that is beign exchanged between the queues.
-
Automatically detect and prevent malicious attacks(probably using SNORT)
For testing whether or not the traffic is being generated locally checkout test-client.js