From 4bba71b8e773032f67242de62fc947d0aa721028 Mon Sep 17 00:00:00 2001
From: CrazeeGhost <21267479+CrazeeGhost@users.noreply.github.com>
Date: Thu, 14 Nov 2024 10:20:14 -0500
Subject: [PATCH] Update README.md
---
README.md | 62 ++++++++++++++++++++++++++++++++++++++++++++++++++++++-
1 file changed, 61 insertions(+), 1 deletion(-)
diff --git a/README.md b/README.md
index 0f80c3c..d77d637 100644
--- a/README.md
+++ b/README.md
@@ -1 +1,61 @@
-# See Notes on individual releases
+## Local PS4 9.00 Jailbreak Host with USB emulation
+This project is aimed at setting up a local web host, with USB emulation, on select Raspberry Pi boards that can be used to exploit and jailbreak PS4 consoles running firmware version 9.00. Raspberry Pi Zero W / Pi Zero 2 W / Pi4 B are eligible boards as they support a USB on-the-go (OTG) gadget mode and eliminate the need to manually insert and remove the USB stick required in the exploit process. This project is implemented on a clean Raspberry Pi OS (Debian) install which makes it easier to repurpose the Pi to run additional applications and services on it.
+Developed and Tested on Raspberry Pi 4 B but should work on Pi Zero W / Pi Zero 2 W / Pi4 B
+
+### Benefits
+- Clean Raspberry Pi OS install - easy to setup the Pi for other purposes as you desire
+- Easily update exploit, GoldHen and payload files from the web interface
+- One device for local web server and USB emulation
+- One USB cable is sufficient to power the Pi and emulate USB
+- You can leave the Pi permanently connected to the PS4. No need not to remove and plug in a USB stick to run explolit
+
+### Setup - Easy Method
+1. Write the image provided in the releases to an SD card (using program like Pi Imager or Rufus)
+2. Insert the SD card into the Raspberry Pi
+3. Optional - If you want to use a different GoldHen version, copy the desired goldhen payload to `/boot/payloads/goldhen.bin`
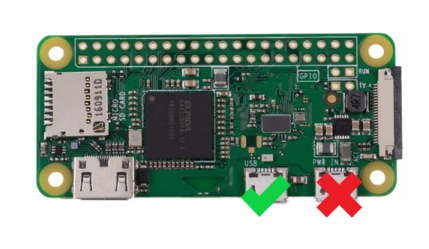
+4. For Pi Zero W & Pi Zero 2W, connect the USB marked Pi USB port to PS4. Be sure to use a cable that supports data transfer
+ 
+5. For Pi4 B, connect a USB C cable from Pi to PS4
+6. For wired connection, use an ethernet cable to connect the Pi to your internet router
+7. Power up the PS4. This should also boot up your Pi
+8. Use `raspi-config` to expand the filesystem to the capacity of your SD card
+9. Use `raspi-config` to connect Pi to your wireless network (if you didn't setup a wired connection in step 5)
+10. For SSH access, username is `pi` and password is `ps4free`
+
+### Setup - Advanced Method
+1. Install a clean Raspberry Pi OS image to an SD card (Developed and tested on Debian Bullseye)
+2. Enable USB Gadget Mode on the Pi
+ a. Add `dtoverlay=dwc2,dr_mode=peripheral` to the `[all]` section inside `/boot/config.txt`
+3. Prevent the Pi from automatically becoming a USB gadget on every boot
+ a. Add `sudo /sbin/modprobe -r g_mass_storage` to `/etc/rc.local`
+5. Install and setup `lighttpd` and `PHP`
+6. Enable fast cgi module for lighttpd
+ a. `sudo lighttpd-enable-mod fastcgi fastcgi-php`
+ b. `sudo systemctl reload lighttpd.service`
+8. Configure `/var/www/html/ps4` as the document root directory for the exploit app (via `lighttpd` configs)
+9. Clone or download the source code from this repo
+ a. `cd /home/pi`
+ b. `git clone -b webkit --single-branch https://github.com/CrazeeGhost/PS4JbEmu.git`
+ c. `sudo git config --system --add safe.directory /home/pi/PS4JbEmu`
+10. Allow the webserver user to run modprobe as root without password
+ a. Add `www-data ALL=(ALL) NOPASSWD: /sbin/modprobe` to your sudoers file using the `visudo` command
+11. Make the web app accessible to the webserver (will not work if you did not follow the directory strcture in step 8)
+ b. `sudo chmod 755 /home/pi/PS4JbEmu/updateHost.sh`
+ c. `sudo /home/pi/PS4JbEmu/updateHost.sh`
+12. (Optional) Enable auto-updates via cron
+ a. `sudo crontab -e`
+ b. `*/30 * * * * /home/pi/PS4JbEmu/updateHost.sh`
+
+### Running the exploit / jailbreak
+1. On the PS4 go to Browser and visit http:///ps4
+2. Click on the GoldHen button for the version you want to exploit with
+ a. A popup will be thrown saying USB emulation started and wait for ps4 pop up
+ 
+ b. Once the USB message disappears, Click ok
+ c. GoldHen will load automatically
+
+### Credits
+1. Kameleonre_ - Porting PSFree Exploit
+2. Sleirsgoevy – Webkit, Offline Activator
+3. Chendochap – KeExploit
+5. PaulJenkin – Inspiration for USB Emulation